From intellectual property to personally identifiable information (PII), credit card numbers, passwords, and more, just about every business and government agency has data that, if compromised or stolen, could pose substantial risk and liability.
In the era of remote work, where connectivity is king, our digital lives are constantly on the move. But as we hop from one Wi-Fi network to another in pursuit of productivity, we often encounter a silent cybersecurity threat - captive portals. These seemingly harmless login screens that greet us in coffee shops, hotels, airports, and other public places can be the gateway to a vulnerability zone we never knew existed.
Captive portals, designed to provide controlled access to the internet, have become a ubiquitous part of our connected world. While they offer free or paid internet access, they also harbor hidden risks that could compromise your personal and professional data. In this article, we will explore the world of captive portals, understand the potential security vulnerabilities they pose, and learn how to protect ourselves while working remotely in the captive vulnerability zone.
One common solution used to address this problem is a VPN, however contrary to popular belief, almost all VPNs do not protect against one of the biggest risks your employees will confront when working remotely - captive portals.
🔎 Related Articles: Future-Proofing Remote Work for Government Employees
What is a captive portal?
When you go to places with free guest Wi-Fi access, you'll typically get a popup web page as soon as you connect to the Wi-Fi network that asks you to agree to terms and conditions and/or put in information like your social media accounts, email address, access code, last name, room number (such as in a hotel) or other identifying information before granting you broader access to the network.
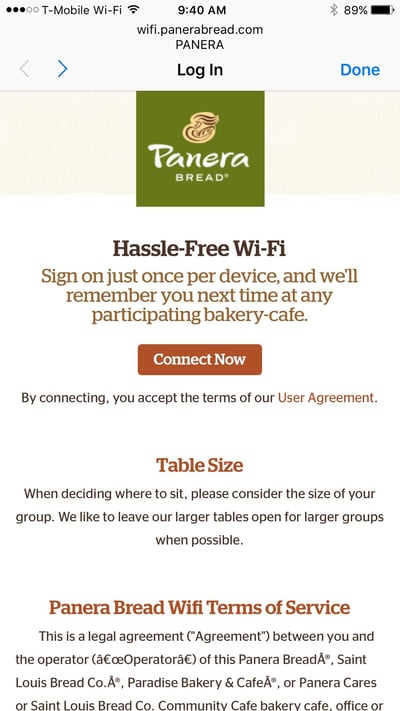
This web page is called a "captive portal" and is used by the establishment offering the Wi-Fi for a variety of reasons that may include verifying users, authentication, controlling the amount of bandwidth being used, reducing their liability in the event of illegal or otherwise inappropriate online behavior, and confirming that users have agreed to terms of service before accessing the internet.
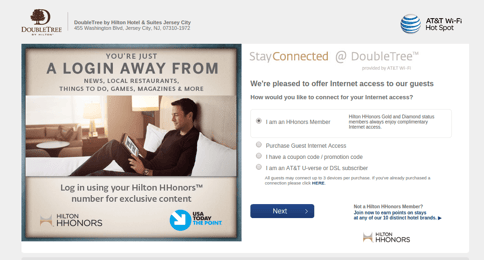
Captive portals can also be used as marketing tools by requiring users to fill out a survey as part of their experience, showing advertisements, or highlighting promotions run by the host establishment.
Here's how a captive portal typically works:
-
Connection to Wi-Fi Network: When you attempt to connect to a public Wi-Fi network, your device will initially establish a connection to the network, but you won't have full internet access yet.
-
Redirect to Captive Portal: After connecting to the Wi-Fi network, your device is automatically redirected to a specific web page, which is the captive portal. This page might ask you to agree to terms and conditions, enter a password or code, sign in with your email or social media account, or make a payment to access the internet.
-
Authentication and Authorization: Once you've completed the required actions on the captive portal, the system authenticates and authorizes your device to use the internet on that network.
-
Full Internet Access: After successful authentication, you gain full access to the internet and can browse websites, use apps, and perform online activities as usual.
Captive portals are used for various purposes, including:
- Access Control: To ensure that only authorized users can use the network.
- User Authentication: To track and monitor user activity.
- Terms of Service Agreement: To make users agree to specific terms and conditions.
- Marketing and Advertising: To display ads or promotional messages.
According to research by Intel, 38% of users regularly choose to use unsecured public Wi-Fi (including networks with captive portals) rather than their own cellular data providers in order to save money on wireless network access, making it highly likely that remote employees will at some point choose to use a captive portal to gain access to the internet.
What are the risks associated with captive portals?
Captive portal authentication provides an easy point of entry for malicious actors looking to gain entry to a guest user's device and, through that, the larger corporate network.
The fact that users' devices must automatically load the captive portal web page, and the associated javascript, directly on their device before accessing the internet means that they are essentially putting their security in the hands of the network administrators who manage that particular public Wi-Fi network.
If the network has already been hacked, or they are running firewalls or other network equipment that is vulnerable, you're essentially giving hackers direct access to your laptop, tablet, or smartphone when you load that captive portal login web page. This kind of access point can be used to execute Man-in-the-Middle (MitM) and Man-in-the-Browser (MitB) attacks.
For example, there have been a number of campaigns (including DarkHotel, which was first uncovered by Kaspersky Labs, and a vulnerability in Inngate routers, discovered by Cylance, which was used to target guests at high-end business hotels) whereby malicious actors have hacked into networks of hotel chains thereby gaining access to the wireless networks the hotels provide.
This makes it easy for them to access the devices of hotel guests. As soon as the guest connects to the network, the malicious actors are waiting. They still have to find a known exploit or zero day, but they don't have to go through a VPN or firewall, because all of that isn't even up yet.
In addition, it is relatively easy for hackers to create their own Wi-Fi hotspots that spoof legitimate captive portals. These phony pages, known as “evil twins”, trick users into connecting to them and then route traffic through their networks where the malicious actor can intercept authentication credentials, and gain access to valuable data and corporate communications. Wired Magazine detailed a recent example of how Russian state-sponsored hackers did just this in a bid to gain access to a wide range of targets relating to the 2016 and 2018 Olympics. They can also route users through a redirect url to execute additional malicious activity.
In another case, X-Force IRIS researchers identified a campaign in the fall of 2019 whereby attackers focused on routers commonly used with captive portals to deliver JavaScript injection attacks with Magecart 5. The activity appears to be aimed at stealing users' payment data.
In many cases, hackers aren't as interested in the user's laptop or personal information as they are in gaining access to the resources they are connected to, including data on the corporate network.
The lesson here? Assume that all public Wi-Fi networks are insecure and take measures accordingly.
Does a VPN protect you from a captive portal?
Most organizations that prioritize cybersecurity install software VPNs on users' laptops, smartphones, or whatever devices they are using for work.
VPNs - or virtual private networks - function as an encrypted tunnel to a server located somewhere on the internet. Because the traffic (data and communications) that passes through that tunnel is encrypted, it is safe from malicious actors.
While VPNs are highly effective in protecting users' devices and data, they typically take about 60 seconds or more to establish a connection.
In addition, the user's device will be on the network for at least 120 seconds while they attempt to authenticate with the captive portal. The problem here is that this is all before the VPN attempts to establish a connection.
It's during that 180 second "captive vulnerability zone" that is where the risk comes in.
If you look at how much network traffic a Windows or Mac laptop generates in that 180 seconds, it is tremendous. The first step a hacker needs to accomplish to gain access to a victim's device is reconnaissance, or learning the software and version that user is running. From there, the hacker simply needs to find a known exploit or potential zero day.
Unfortunately, the 180 seconds that it takes for a VPN to go live is plenty of time for a hacker to accomplish these things and compromise the user's device. Worst case, they can gather the reconnaissance information, find the exploits, reset the user's Wi-Fi connection to bring down their VPN, and then exploit the user's device.
Any time a user logs on to the internet via a captive portal, they have to trust that the location or establishment where they are accessing the internet is protecting its infrastructure properly -- and in many cases, they are not.
That means that during the 180 second "captive vulnerability zone," the user is completely vulnerable - and it's during that time that, despite using an enterprise-grade software VPN, malicious Java Script could be loaded onto the user's device without them even knowing.
🔍 Read Now: The Ultimate Hardware VPN Buyer's Guide
Why hasn’t this challenge been solved already?
The main thing standing in the way of solving the captive portal challenge is the lack of standardization in the way that captive portals authenticate users.
Because every hotel, café, coffee shop, airport or train station may be using a different system for its public Wi-Fi network, it's difficult (if not impossible) to create an automated solution for secure authentication.
The only solution that we at Archon are aware of that completely protects a user from captive portals (other than simply not using them) is captive portal isolation.
What is captive portal isolation?
Captive portal isolation involves the use of a combination firewall and hardware VPN with a built in, stateless sandboxed web browser. It works as follows:
-
The user connects, via Wi-Fi or Ethernet, to the hardware VPN;
-
They then use the hardware VPN to connect to the internet (in this case, via a captive portal);
-
The stateless sandboxed web browser that is built into the hardware VPN is actually what loads to the captive portal, and it then presents a screen capture of the captive portal on the user’s device;
-
In this manner, the captive portal web page never actually loads on the user’s device and the firewall prevents the malicious actor from gaining access to user data or communications.
The primary purposes of captive portal isolation are:
-
Enhanced Security: By preventing direct device-to-device communication on the network, captive portal isolation reduces the risk of unauthorized access and potential attacks between devices connected to the same network. This is particularly important in public Wi-Fi environments where security is a concern.
-
Privacy and Data Protection: It helps protect the privacy of users by minimizing the risk of data leakage or eavesdropping between devices. Users on the network are isolated from each other, making it more challenging for one user to intercept another user's data.
-
Network Segmentation: Captive portal isolation effectively segments the network into isolated "zones," ensuring that even if one device is compromised, it is difficult for an attacker to move laterally and compromise other devices on the same network.
Archon’s GoSilent Cube is an example of a combination VPN, firewall, and Wi-Fi hotspot that is capable of isolating captive portals in the manner described here.
What’s the best way to protect your data when using captive portals?
Of course, the best way to protect your data when using captive portals is to not use them at all.
While that is the best solution, it is not the most practical, and in reality, users will likely continue to turn to public Wi-Fi when they are working remotely, and often this is one of the primary reasons government agencies don't allow remote work.
That being the case, there are a few things that you can do to ensure that your employees practice good cyber hygiene when in a remote work environment:
-
Make sure that all software on user devices is updated and patched;
-
If your employees will be using a software VPN to connect to the internet, make sure it is set to establish a VPN connection as soon as a network or internet access is found (most enterprise-grade software VPNs have a setting for this); and
-
Many VPNs offer an option called “split tunneling,” whereby only work-related traffic goes through the VPN and the rest of the data goes through the public internet. Sending ALL traffic through the VPN provides the maximum level of isolation that you can get with a software VPN. If you’re not doing this, you’re effectively pushing your security risk down to whatever Wi-Fi network you’re using -- so your users will only be as secure as the network they’re on.
The bottom line is that it doesn't take long for a hacker to gain access to a user's device when they're using a captive portal. And once they access that device, it can act as a back door to the real prize, which is your corporate network, and potentially the networks of your partners and/or supply chain.
If your employees work remotely, it's critical that you take steps to ensure they can do so securely from wherever they choose to connect to the internet.
