What is a Next Gen VPN?
A Next Gen VPN is an evolution of both network architecture and VPN technology that provides a greater degree of control and thus improved security, in access to both cloud and centralized network resources (or a hybrid of both).
Much like with Zero Trust, the things that will set Next Gen VPNs apart from current or traditional VPN technology include:
-
They will default to deny access (or grant zero trust) for ALL users.
-
They will follow a least-privilege access model, only granting users and devices access to the applications, services, and data that are absolutely necessary for their role within an organization (rather than full access to the network as a whole, like current VPN technology).
Some of the requirements of the technology itself will include:
-
Data in transit: Encryption of the data will be required as it is transmitted from the remote user device to either the centralized network or the cloud environment.
-
Authentication and authorization: Explicit verification of the user, the device, and access privileges will be required to gain access to each individual application and service.
-
Device compliance: Devices themselves will be required to adhere to a set of standards for protection of any data stored or accessed through them.
-
Auditing: A full audit trail of not only VPN logins, but which applications or services they were used to access will be required as well.
To learn more about Zero Trust and Next Gen VPNs, listen to this interview with Michael Sutton, Founder of Stonemill Ventures and former CISO of ZScaler.
🔎 Related Articles: Hardware VPN Buyers Guide
Why do we need to move to Next Gen VPNs?
Let’s step back for a moment and explore why the industry is moving in this direction, and what is fueling the need for Next Gen VPNs.
Some of the common problems or questions that come up today, that can’t be solved by VPN technology as it stands, include:
-
How do you securely share data with third parties and contractors and prevent data loss or compromises?
-
How do you secure remote and mobile workers?
-
How do you provide truly user-friendly remote access?
-
How do you provide secure, scalable communications to thousands of remote IoT devices (e.g. cars, cameras)?
-
How do you securely connect data centers and public/private cloud resources?
-
How do you provide a secure connection to a hybrid cloud infrastructure?
Right now, we may have work-around or “best we can do” solutions for the above use cases, but there isn’t a solution that truly checks all the boxes to make it a great solution.
Traditional VPN technology helps deliver secure communications from a remote location to a central server, but it doesn’t provide the granularity of access control and support for the heavy usage of cloud applications organizations have come to rely on.
Specific to enterprise organizations, we see the following factors influencing the need for Next Gen VPN technology:
-
Increased risk exposure due to the use of cloud-based services.
-
Applications and workloads have been moving more and more to the cloud (e.g. PaaS, IaaS, SaaS).
-
Unrestricted access to cloud storage and workloads poses a significant threat.
-
Private, public and hybrid clouds are all sharing enterprise data.
-
A mobile workforce means remote access is a requirement rather than a “nice to have.”
-
IP-connected devices are being deployed in staggering numbers.
-
Legacy or insecure infrastructures are increasingly being connected to the internet, especially IoT devices.
-
Insider security threats are on the rise, and securing internal critical resources from on-premise users as well as remote workers is becoming important.
-
A lack of IT and security talent and experience, specifically in the areas of automation and managed services, is driving a need for simpler technology.
-
Enterprises must also deal with the risky proposition of providing access to a varied list of contractors, suppliers, partners, customers, and developers. Thus partner identity management and more granular access control for third parties are required.
-
Cyber-attacks, malware, foreign exploitation, and IP Theft are all on the rise, greatly affecting the security of remote access.
The transition from existing VPN technology to Next Gen VPNs
The switch to Next Gen VPNs involves far more than a simple comparison of technologies. Utilizing Next Gen VPNs and gaining all the benefits from them means a gradual overhaul of the entire network architecture and design.
As you can see in the comparison of network diagrams below, from Z-Scaler, the traditional model is one of a network-centric structure in which everything comes back to a centralized, protected network. In this model, securing the network was enough to keep the applications running on that network secure.
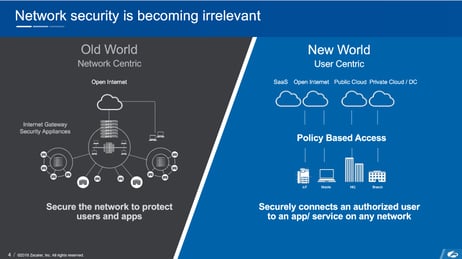
(source)
This is no longer the case.
In today’s connected world, filled with cloud-based applications and a hybrid approach to data storage, the centralized network architecture goes out the window.
Instead, today’s world requires a user-centric architecture where policy-based access controls who can access each of the different applications and storage methodologies employed by an organization.
Building a Zero Trust architecture
To truly build out an architecture that allows for zero trust, you’ll have to consider taking steps to increase your overall level of cyber maturity. It will be very difficult to snap your fingers and have a full zero trust network overnight.
Below is a breakdown of three primary levels of maturity you can fall into, with information on the components your architecture will have to include to fit into that level.
Level 1
Level 1 provides the basics for a zero trust access model with policy-based segmentation. It includes the foundations for identity verification and access controls that can be applied in real time, on every connection request. Devices can be located anywhere (inside or outside perimeter), as can the services they are trying to access (on-premise or in cloud).
Architecture requirements to meet this level of maturity:
- User/device agent
- Identity management (SSO for users)
- Policy engine
- Gateway
- Full audit log for all of the above functions
Level 2
Level 2 builds upon Level 1 to add more robust policy and compliance checks that occur on every connection request.
It includes utilizing the telemetry in devices from agent(s) and services to perform real-time verification and risk assessments and then restricting access based on policy.
Architecture requirements to meet this level of maturity:
-
Device compliance
-
Auth (certificate)
-
Full disk encryption
-
OS version and patch status
-
Malware status
-
Geolocation
Level 3
Level 3 is more of an automated Threat or HUNT capability that can be built upon the audit logs, telemetry, and other data sources available from Level 1 and Level 2. It can be used to refine and improve Level 1 and Level 2 to prevent false positives or explicitly take an action for specific threat actors.
This level uses behavioral profiles of access to automatically alert or flag variances and create an artifact of related security data.
Architecture requirements to meet this level of maturity:
-
Behavioral AI for managing access
Requirements of VPN technology to support Zero Trust
The second half of the equation in building out a true Zero Trust architecture is the VPN technology used to support the architecture changes outlined above.
In order to make the architecture work, VPN technology will need to continue to advance by tightly integrating with existing network security functions or seamlessly providing a combination of features and functionalities.
Some of the primary compliance and policy feature requirements that VPN agents can address in order to be considered Next Gen VPNs include:
-
Security client running
-
Geolocation
-
Time of day
-
Risk level/SIEM alert level
-
Mobile device management/jailbreak status
-
Runtime attributes
-
User patterns of behavior
-
Ensure the device is free of virus or malicious software
-
Management of certificates
-
Multi-factor authentication
-
User’s role, directory group membership
-
OS version and patch status
-
Device encryption
-
Windows registry keys
-
SAML
-
PKI service attestation
-
OpenID
-
Oauth
-
LDAP
-
Kerberos
Some important distinctions in how traditional VPN technology works and how Next Gen VPN technology will work include:
-
Support for IP tunneling: For increased security, Next Gen VPNs will allow for encryption of the entire IP packet (rather than just the data in that packet) to be sent, and then wrapping that inside of an outer IP packet.
-
Fingerprinting: Knowing who is sending what traffic in a VPN network will be very important.
-
Faster configuration and speedier setup times: Reducing the complexity of initial configuration down to two or three parameters and reducing the time to establish a connection will increase ease of adoption.
-
Disguising traffic type: VPN traffic is usually easy to pick out. As such, it becomes easy to recognize and block -- a common practice in countries like China. Next Gen VPNs will have ways to make the traffic sent through them look more like regular internet traffic, thus bypassing potential blockers. They could also change the signature of the IP packet as the data traverses through a network.
Final thoughts
The move to Next Gen VPNs is already in motion. It is an eventuality all organizations will face and have to act on at some point in the future.
The most important thing to keep in mind is that the switch to zero trust is much more involved than simply purchasing VPN hardware or licenses.
Choosing to move through this transition at a walk rather than a run can make it smoother and simpler for your organization.
Consider making architectural changes in stages and moving closer to a Zero Trust architecture over time rather than expecting a wholesale switch at a single point in time.
