In recent years, the government has become increasingly aware of the need to support remote work, and our inability to achieve remote work at the levels necessitated by the current global situation has shined a very strong light on the current gaps in government remote work programs and infrastructure.
Remote work and government agencies
Prior to the COVID-19 pandemic, government agencies would identify a core group of individuals that needed remote work capabilities for continuity of operations. This group was primarily selected due to a role that required them to be connected whenever they work from home or on the road, in the course of normal life circumstances.
Oftentimes, another deciding factor in allowing remote work for individual government employees hinges on what kind of data they access in the execution of their job. The more sensitive the data, the less likely that they would be allowed to access it remotely.
Agencies might also have determined an additional percentage of staff that they might want to be prepared for remote work should the need suddenly arise. In this case, they would have procured the equipment for an additional, say, 10% of their team to be covered. They might not have deployed or set-up all of this equipment, but would have had it available in the event it was needed.
In most cases, the combination of the two groups above would have allowed for a percentage of a particular agency’s staff to quickly be up and running remotely. The remaining staff would be placed on administrative leave and their work halted.
In all of the above cases, the amount of remote work that can be supported relies 100% on the ability to supply government-furnished devices to staff.
And therein lies the problem.
The costs associated with having enough government-furnished devices ready for the entirety of your agency staff is not usually feasible.
More specifically, in this case, where remote work needed to be ramped up very quickly, and with little involvement from the IT staff, this approach is not only impractical but completely impossible.
Combining VDI & VPN
Thankfully, there is another option that is much quicker to ramp up, less expensive, and even more secure.
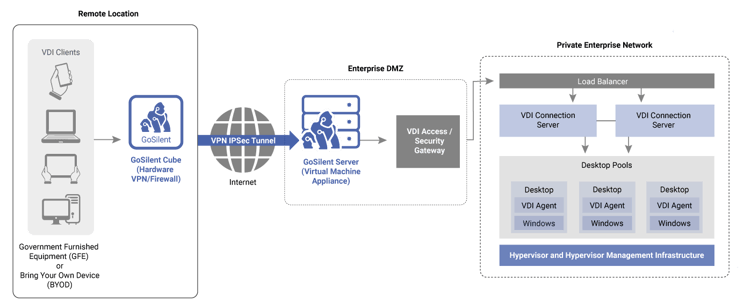
Combining Virtual Desktop Infrastructure (VDI) with a secure hardware VPN can allow your staff to securely connect to your internal network from their own devices, without the need to to procure large volumes of government-furnished devices.
A VDI allows users to work remotely through a virtualized environment that lives on your central server. End user devices connect via the VDI to virtual machines that you have set up on your server, and in this manner, users can execute work as if they are on your internal network.
With VDI, no data is stored on the end user device. Instead, the user can simply see what is on the screen of the virtual machine and interact with it, but not store data from it.
VDI supports a range of end user devices, from laptops and desktops to tablets or mobile devices.
Combining this environment with a secure hardware VPN, like Archon's GoSilent Platform, protects all traffic and information flowing across the connection between the end user device and the central network.
How it works
Setting up a virtualized environment using VDI is much faster, easier and less expensive than outfitting a significant number of government-furnished physical devices for use. All you have to do is go through the following steps to get your environment ready for high-volume access:
- Build a template virtual desktop image that has the operating system set up and locked down the way you’d prefer, and install any components or software that your user base might need to execute their jobs.
- Use the template image to build as many individual virtual machines desktops as you need. Setting this up on the order of 10,000 virtual desktop instances can be done in a matter of hours.
To ensure that users are accessing their virtual machines securely, and that no data can be compromised or accessed through eavesdropping, you’ll need a hardware VPN that ensures all virtual desktop traffic is delivered over a secure, encrypted channel. A NIAP approved solution will ensure that you are covered all the way up to the most sensitive data.
Why a hardware VPN?
In this case, a hardware-based VPN solution is far more attractive than a software-based VPN because you need a device-, operating system- and software-agnostic solution that can work with employees' personal devices (ex. computers, smartphones, tablets, etc.).
You’ll never be able to control the varying devices, frequency of updates and software versions across all of your users’ personal devices, and you’ll need a solution that can provide a secure connection, regardless of the state of those devices.
Outfitting your network and users for secure access can also be accomplished much more efficiently and with a lower overall cost than setting up laptops for each user.
As an example, doing this with Archon's GoSilent involves the following steps:
- Set up server-side VPN components on your internal network to allow for VPN connection into your network. This can be set up and complete in as little as 10 minutes.
- Provide each user with a GoSilent Cube that allows their device to connect securely over the open internet to your internal network. (In today’s COVID-19 environment, it is very easy to ship these small devices directly to users).
- Users connect their GoSilent Cube to their devices (with no setup required for a simple, plug-and-play solution that even non-technical users can complete in just a few minutes), download the agency-determined VDI application, login and go!
Benefits of combining a VDI & hardware VPN solution
The primary benefits of executing a solution like this are:
- BYOD can become a reality for government agencies: Prior to this, Bring Your Own Device (BYOD) was simply not a solution that was ever even considered for government agencies. An architecture like the one outlined here allows for the use of personal devices with no risk to your data.
- Faster to implement: Getting a solution like this up and running can happen very quickly, and with little involved effort by your IT team. When compared with setting up and deploying laptops for every member of your staff, this is close to an instantaneous solution.
- Better technical investments: Either type of solution requires an investment in technology to achieve. However, the combined VDI and VPN solution will be less expensive overall and the technology you are investing in will be highly repurposable or reusable if you need to make a change. Reusing server space and device-agnostic VPNs is much easier, as each has a far greater number of applications, than reusing a laptop.
- No risk to your data: Because no data is ever stored on an end user device, and all of the changes or modifications to your data are happening physically on your servers (inside your network, inside your secure facility), it is actually more secure than providing government-issued devices, which can be lost or stolen, to your employees.
- Significantly lower management and maintenance: Managing the updates, patches and setup of the combined VDI and VPN solution is next to nothing compared to the effort involved in managing patches and updates on tens or even hundreds of thousands of laptops.
The future of remote work for government agencies
As this pandemic has taught us, we need to be better prepared for situations which would require our entire staff to work remotely. As such, there will be big and lasting changes coming that will force government agencies to have better plans in place for remote work.
Because a combined VDI and VPN solution is faster to deploy, easier to scale up and down as needed, and is actually more secure than other current methods in place to support remote work, it is perfectly poised to change the way the government approaches remote work in the future.
