Commercial National Security Algorithm (CNSA) Suite Encryption
CSfC Approved Solution for Remote Access
The Commercial Solutions for Classified (CSfC) program was established in order to enable U.S. government agencies and their customers to take advantage of affordable and readily available commercial off-the shelf (COTS) IT solutions that meet the NSA’s stringent security guidelines for the transmission of classified data.
Archon’s GoSilent is certified as an IPsec VPN Gateway and allows you to achieve a secure remote access solution that fits within the CSfC Mobile Access Capability Package.
How it Works
The NSA Capability Package for mobile access calls for three firewalls, Red (inner tunnel), Gray (middle tunnel) and Black (outer tunnel) and encryption as shown here.
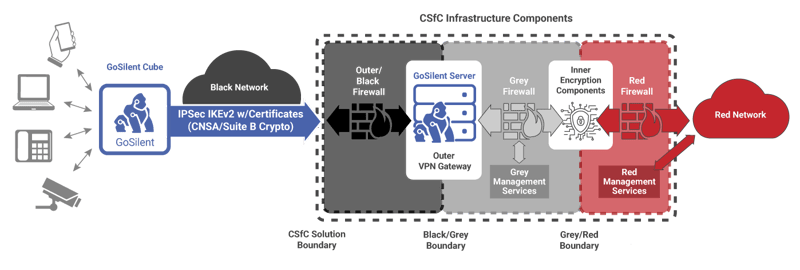
GoSilent meets the NSA criteria for mobile access and offers a dedicated, plug-and-play outer VPN and firewall, thereby eliminating the need to download and integrate software for both outer and inner VPNs.
You can also integrate seamlessly with any previously installed software such as Microsoft Outlook. The outer tunnel meets IPSec IKEv2 standards with CSNA Suite B encryption. GoSilent’s layered protection enables classified communications anywhere at any time – even over public WiFi.
CSfC Certification Information and Resources
Top Secret Level Security
GoSilent is the first portable product to be given this level of certification.
Double Encrypted
The NSA sets strict criteria for accessing classified networks.
Secure Over Any Connection
NIAP certified solution for classified and unclassified communication even over the public Internet.
Highly Portable
GoSilent meets the NSA criteria for mobile access and can be used from anywhere.
Compatible with 4G and Satellite
GoSilent works on any IP-enabled network, including cellular and satellite networks if required.
CNSA Level Encryption
Built to CNSA Encryption standards and approved by the NSA to protect information at a classified, top secret level.
Dual Encryption Tunnels
For the highest level of protection, a virtual private network (VPN) creates a secure link with the first of three firewalls. The first sits in the “outer tunnel”, the second sits in the “middle tunnel” and the third in the “inner tunnel”. Before entering the IPSec tunnel, the data is encrypted twice.
Encrypted data packets travel from the device through the first firewall. If they are found to meet the security parameters, they are encrypted a second time by the outer VPN and by the inner encryption component. Then, once received, the data packet is decrypted twice by the inner encryption component and the outer VPN. The outer tunnel or “black network” may be operated by an untrusted third party and connection may be made through public WiFi. Products that meet the CSfC standards associated with this technology combination of firewall and encryption are certified for protecting NSS data.
Data Encryption Standards
The Commercial National Security Algorithm Suite (CNSA Suite) provides new algorithms for those customers migrating from Suite B algorithms. CNSA Top Secret (TS) level encryption is the same technology used by U.S. government agencies like the NSA, DoD and other governing bodies. Previously known as Suite B, military-grade or classified federal government standard, Advanced Encryption Standard (AES) 256-bit end-to-end encryption is the most secure solution in the marketplace. AES-256 is the first publicly accessible and open cipher approved by the NSA to protect information at a classified, top secret level.
With over 14 rounds of encryption, each 256-bit encryption key scrambles the data and divides into 128-bit blocks. The number of possible keys in the AES 256-bit encryption is 2 to the power 256 (a 78-digit number), making the code virtually impossible to crack by brute force attack.
Additionally, with Top Secret level encryption, both the sender and the receiver must know and apply the same secret 256-bit key. The key is never stored on any server, and only those communicating have access.
GoSilent utilizes AES 256-bit encryption to protect your private data and keeps it fully encrypted end-to-end. Data is never stored on an intermediary server. In keeping with Top Secret level encryption standards, there are no extra keys. Archon Security does not record, copy or have access to the encryption codes. This means that your data remains secure, even if compromised.
Contact us
