Federal Information Processing Standards (FIPS) Compliant
FIPS Compliant Solution for Remote Access
Only FIPS 140-2 compliant solutions may be deployed to work with federal government departments that collect, store, transfer, share and disseminate sensitive but unclassified (SBU) information.
Archon'sGoSilent portable VPN and firewall offers robust encryption protection algorithms and design and is FIPS 140-2 certified.
Encryption for U.S. Government Agencies and Contractors
GoSilent deploys AES 256-bit encryption to protect sensitive data via dual tunnel, end-to-end encryption. Data never gets stored on an intermediary server, and no extra keys are ever generated.
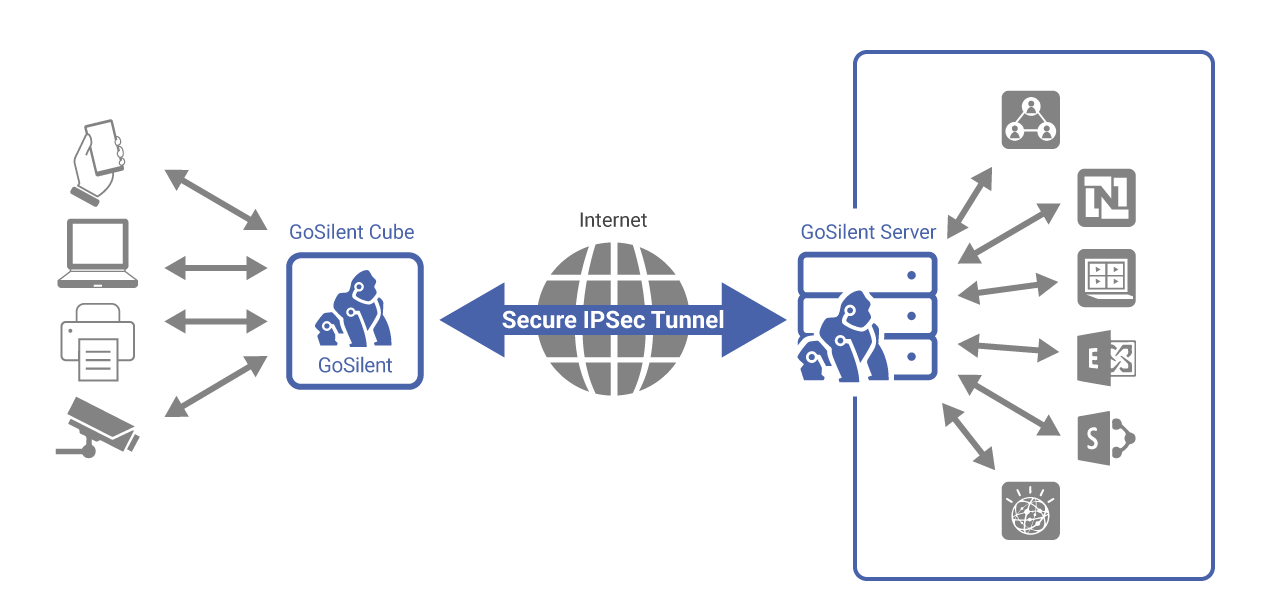
Using two nested, independent encryption tunnels helps to protect the confidentiality and integrity of data as it moves through an untrusted network. Each of the two tunnels helps protect data flow by using one of two independent encryption protocols:
Internet Protocol Security (IPsec) generated by a Virtual Private Network (VPN) Gateway
Media Access Control Security (MACsec) generated by a MACsec Device.
The outer tunnel of a dual tunnel VPN refers to the components that terminate the outer layer of encryption.
GoSilent utilizes AES 256-bit encryption for the outer tunnel to protect your private data and keeps it fully encrypted end-to-end. Data is never stored on an intermediary server. In keeping with Top Secret level encryption standards, there are no extra keys. Archon does not record, copy or have access to the encryption codes. This means that your data remains secure, even if compromised.
FIPS Certification Information and Resources
What does FIPS Certification Mean?
Is FIPS Compliant the same as FIPS Certified?
IT security solutions that are marketed as being FIPS compliant are making a claim that the product meets FIPS requirements. However, this is very different than if a NIST-approved laboratory validates that the product meets FIPS requirements.
During FIPS certification, the file transfer software and client and server applications are each independently tested to confirm they meet FIPS standards and are also checked for security vulnerabilities, predictable number generation and reckless disposal of keys.
Learn More
Contact us.
