The Complete Guide to IoT Security
Everything you need to know about securing your IoT deployment.
No time? Get the PDF sent to you via email.
What will you find
in this guide?
This guide is built to help organizations looking to implement IoT solutions as well as IoT integrators.
This guide will help you learn about:
- Different designations of IoT, including IIoT
- Primary security challenges for IoT deployments
- Overcoming issues with legacy technology
- Architecture options for IoT and IIoT deployments
- Tools and options for securing IoT solutions
Most organizations or integrators looking to implement an IoT solution already understand the basics. This guide does have some background to provide context, but will get right into the meat of how to build your IoT solution architecture.
The Internet of Things is a term representative of the industry shift to connect as many different people and devices as possible through the internet for the purpose of making life (or work) easier, more convenient and more effective.
The Internet of Things, or IoT, is a concept that has been around for many years, but most credit the official phrase to Kevin Ashton, who coined it in 1999. Researching IoT will generate plenty of technical information and detailed descriptions, but at its core, IoT is designed to connect the things we use on a day-to-day basis to the internet to make life (or business) easier.
One of the simplest explanations comes from IoT for All: “The Internet of Things is actually a pretty simple concept, it means taking all the things in the world and connecting them to the internet.”
Since the inception of the phrase in 1999, IoT has taken off and now boasts huge industry events, large divisions at major technical corporations and an entire marketplace of connected products and services.
IT vs. OT
As part of understanding IoT security, it is important to also understand the distinction between IT and OT.
- Information Technology (IT): IT networks deal with the flow of data or information across an organization.
- Operational Technology (OT): OT networks manage the operation and control of physical processes and machinery.
There is plenty of debate about the integration of IT and OT. Many believe that bridging the gap between the two is important, while some strongly maintain that they should remain separate.
What is most important when considering cybersecurity as it relates to IoT is to find a way to transfer information between IT and OT networks while segregating control and access to OT networks in order to maintain secure control of the technology controlled by those networks.
At a more detailed level, IoT breaks into a couple of major categories.
Depending upon your level of technical involvement in the IoT industry, you may or may not realize all of the things it truly encompasses. When you think about the broadness of the term “Internet of Things,” it is no surprise that you can make the argument that just about anything that connects to the internet falls under the umbrella of IoT.
The three broad categories that most experts would agree comprise the commercial IoT space include:
- IT Systems
- Operations & Predictive Maintenance Automation
- Connected Products
IT Systems
Sometimes this group is considered part of the IoT space and sometimes it is excluded. Depending upon who you talk to, the definition of IoT is very fluid. But, because it does include all “things” that connect to the internet, we do want to consider this category.
While many might not traditionally count endpoint devices that are user controlled, rather than autonomous devices, as part of IoT, we will address them in this guide. You’ll see examples of IoT deployments geared towards human end users as well as endpoint devices below. Feel free to pay attention only to those that are relevant to your area of interest.
IT Systems are exactly what they sound like, back-end IT infrastructures for business. It would include all of the architecture used to house and access data for your organization like servers, virtual servers, endpoints, etc.
Most commonly, the area of this category that is most heavily considered “IoT” would be remote connectivity to a primary network. This means that you have disparate endpoints all needing to communicate back to a primary network across the open internet.
Many large organizations require highly secure, robust systems and architectures for executing remote access. As such, enterprise IT systems and remote access are amongst the largest subsegments of the IoT industry.
In this particular category, IoT security is a huge concern. Remote access to a corporate network is riddled with opportunities for compromise and loss of sensitive data. The more regulated an industry or organization, the higher the degree of emphasis on cybersecurity is required by their enterprise remote access solution.
A very large number of network breaches can be traced directly back to remote access as the point of entry.
Operations & Predictive Maintenance Automation
Another common application of IoT in a business setting is for operations and process support, wherein sensors are embedded across an organization’s infrastructure to create an Iot ecosystem for a variety of purposes, including:
- Fleet management and tracking
- Equipment monitoring and maintenance
- Inventory management and tracking
- Productivity or throughput measurement
- Anomaly detection or data gathering
This category of IoT is often referred to as Industrial IoT or IIoT, and is really centered around connecting internal equipment and devices to a centralized network for the express purpose of improving operations in some capacity.
Some of the goals of IoT deployments in this category include:
- Improving productivity
- Mining data to make product or process improvements
- Tracking valuable assets
- Staying ahead of maintenance requirements
- Improving equipment performance or longevity
- Managing security or compliance requirements
- Reducing manual work for human resources
This particular category of IoT has seen an explosion in recent years and will continue to grow as the area matures.
When it comes to operations and predictive maintenance automation, security is a significant concern. The data being transmitted by these types of IoT solutions is almost always proprietary and in some cases, compromise of that data could have very serious consequences.
Breaches to industrial IoT networks are becoming more common as more organizations mobilize IIoT initiatives.
Connected Products
This is the category people most associate with the term “Internet of Things” and is arguably the most well-known. This area of IoT includes all individual products or devices that are connected back to a centralized service source over the internet.
The age-old example of a connected device is the refrigerator that orders more milk when you run out.
Many of the devices, such as smartphones, smart watches, and Alexas, that are core to the way we live our lives every day fit into this category.
With respect to connected products, cybersecurity concerns can vary significantly depending upon the application of the product and the information it is sending. For instance, if I’m just sending exercise-related data on the number of steps I take a day back to the cloud, I may not be overly worried about that information falling into the wrong hands.
On the other hand, if I have a product that is deployed in the financial industry that sends banking or account data, it had better be incredibly secure.
2019 alone saw some very high profile connected product breaches that shed light on the drawbacks of cyber security in IoT.
There are quite a few significant challenges with IoT security, but on the whole, what makes IoT security such a massive subject are the sheer number of different use cases, deployment options, types of architectures, and needs of different IoT deployments.
This means that individual security concerns or challenges for your particular IoT security solution will be unique to the goals of that initiative and the restrictions you have on technology or deployment options.
In general, there are five main categories of challenges that make IoT security difficult to tackle:
- Number of endpoints
- Architecture options
- Manned vs. unmanned systems
- Consequences of a breach
- Cost and ROI
IoT Security Challenge #1: Number of endpoints
One of the most obvious difficulties with tackling the subject of IoT security is in the sheer number of endpoints that may need to be secured. Most of the time when IoT is used in a business setting, we are talking about very large numbers of devices that ultimately need to communicate back to a centralized network.
Securing a single endpoint is relatively straightforward, but when it comes to scaling security for a large number of devices, and considering the costs associated with doing so, security suddenly becomes a very complex conversation.
IoT Security Challenge #2: Architecture options
As the saying goes, “there are multiple ways to skin a cat.”
Nowhere is this more true than with IoT deployments.
With each different IoT goal or deployment type, there are usually many different ways an organization could choose to approach building and securing that particular initiative.
The challenge really comes in a couple of different ways:
- Knowing all of the potential options: Because there are so many different tools and technologies available, and so many different ways to combine them to create a final solution, the challenge comes in having a single person (or even a team) that has the breadth of expertise and experience that will allow them to consider all the potential possibilities you have for a solution.
- Comparing all of the potential options: If, by some miracle, you are able to come up with all the possible solutions that would be a fit, comparing them is still a sizable chore. You have to consider how much the solution will cost, how it will scale, and how it will fit within your current environment.
This particular challenge is exactly why IoT Integrators exist. They have the technical knowledge, expertise and experience across a wide variety of deployments to help surface all available options and narrow down to the best fit.
What is an IoT Integrator?
An IoT integrator is a service provider that can help design, architect and build an end-to-end IoT solution.
IoT Security Challenge #3: Manned vs. unmanned systems
Another huge challenge with IoT is that you are dealing with endpoints that can be either manned or unmanned.
Manned endpoints have a whole host of human error related problems, where you are often relying on an end user to understand how to configure and maintain something like a software VPN correctly in order to keep a solution secure.
Any IT support person will tell you that relying on humans for anything, particularly when it comes to technology, is a scary prospect.
On the flip side, you also have to deal with unmanned systems, which means no human to remember and provide a password to authenticate a device. It also means that there is no one there to make real decisions if something needs to be changed, reconfigured or go through troubleshooting.
With IoT deployments, you have to deal with all of the security challenges of, and consider security solutions for, both cases.
IoT Security Challenge #4: Consequences of a breach
Another big subject in the mix for every IoT deployment is the consideration of what the consequences of a breach to the data an endpoint sends, receives or stores really means.
The consequences of a breach can vary significantly across different use cases, but in some cases can be incredibly dire.
Depending on the application, a breach in an IoT environment could mean something like leaking of important information that is critical to the way your business works or a device is manufactured. On the larger side, in instances where that device is controlling manufacturing or part performance, it could mean compromise of the product you produce.
Take an industrial IoT example, like bolt manufacturing.
If a hacker gained access to the network for your bolt manufacturing plant and changed the machine settings that controlled the strength of that bolt, it could easily cause bolts to fail and your products to fall apart under stresses they should normally be able to withstand.
At worst, that could mean a person dies when your product fails.
While the risks may vary depending upon how you use IoT devices in your organization, the threat is real no matter what the level of concern.
In other cases, concern for unauthorized access to the information on a device may be very low, and this particular challenge may not be something you have to put much focus on.
A survey of 700 IoT security decision makers, conducted by Vanson Bourne, showed that upwards of 80% of those organizations experienced a cyber attack against their IoT solutions over the last 12 months.
While the costs of an IoT breach can vary, an attack that hits the right devices can be incredibly costly. For instance, an attack on a Taiwanese TSMC chip fabricator’s IoT network resulted in costs upwards of $170 million.
IoT Security Challenge #5: Cost and ROI
All of the above different challenges really roll up into one big and final challenge, which is weighing the cost of your initiative with the ROI of executing and the ongoing risks of allowing connectivity.
Ultimately, the solution you choose needs to provide enough value to cover the cost of implementing and managing it.
In addition, you’ll have to weigh the costs associated with securing your solution against the benefits of having the data available and the consequences associated with a breach.
Now that we’ve examined the challenges IoT security poses, let’s take a look at some of the specific IoT security issues that arise when looking to secure these technologies.
IoT Security Issue #1: Legacy Hardware and Software
The number of IoT devices has exploded in the last several years, with many organizations looking for opportunities to connect devices across a range of business processes to improve operations, increase opportunities for revenue, or get access to valuable business data.
The problem is that in many industries, the devices that collect this data, and the networks they must communicate over, are outdated, past their prime, or downright primitive by today’s standards.
Legacy Hardware
You can divide the types of IoT device assets currently in use today into two classes. There's the class of assets that were built and never expected to be IoT devices. And then there is a second category -- devices which were built specifically to collect data and be used for IoT purposes, but they themselves may be outdated at this point.
The first category includes plenty of industrial IoT examples: equipment or machinery that has been in use for decades, and works just fine, that suddenly needs to be network connected. These include things like cutting machines, mixing machines, pumps, boilers and compressors used in many manufacturing operations today.
The truth of the matter is that legacy systems aren’t going away any time soon, so finding appropriate ways to work with them is key.
Legacy Software
Not only do you have to worry about the physical technology in use at endpoints, but many of the networks in use, particularly in industrial IoT use cases, rely on outdated technology as well.
In many cases, the network protocols and methods for storing and sending data that these sensors connect aren’t supported by modern network technology.
Many applications require industrial connections for sensors, like Modbus, Profibus, EtherCAT, CAN bus, and many more. It's an alphabet soup of various protocols that have been created in siloes over the years.
Again, this means that the solutions we choose to implement will have to work with the existing software environment.
Read the Article: IoT Security Issues: Legacy Hardware and Software >>
IoT Security Issue #2: Disparate physical locations
Depending upon what kind of IoT application you are considering and the devices you’d like to connect, you may be looking at connecting devices that encompass a very large geographic footprint.
This makes securing the connections and communicating with those devices especially challenging, and in some cases may mean relying on networks that are, at their very core, untrustworthy.
You may find yourself in a situation where you have to rely on connections like:
- Networks with untrusted devices: In cases where end user devices need to connect over networks that will likely have many other untrusted devices on them (think home Wi-Fi networks), the same benefits apply to hardware-based security solutions.
- Cellular networks: Some geographic locations may even require the use of LTE, 4G or 5G connections to reach devices. In this case, costs can be a concern and the data you send to those devices still must flow through the cellular network and towers. By their very nature, cellular connections have the same, and potentially even higher, risks than public Wi-Fi connections.
IoT Security Issue #3: Physical security
You also have the added concern of the physical security of the device itself. If the device were to be stolen and the data stored on it accessed, what would the consequences be?
So, which cyber security solutions can help with IoT physical security?
Often, we find that the most secure solution is the obvious one: don’t store information on devices. A deployment that keeps secure data on a centralized network, and not stored on the device itself, makes for a simple and effective solution to this challenge.
In cases where this isn’t possible, due to intermittent connectivity or cost concerns, device encryption is the best way to protect any data stored on the device itself.
IoT Security Issue #4: Remote access
Another, much newer, concern is the ability to remotely access and control these connected devices as a human user. As current times have shown us, the need for organizations to work remotely is at an all time high.
While remote work is not a new concept in a traditional office environment, we are now seeing telework begin to infiltrate the industrial IoT space as well, with manufacturers looking for ways to give employees remote access to control plant equipment, allowing them to do their work from anywhere.
Allowing for remote access in which a user needs to control a device or access a central network brings with it all of the problems that human behavior introduces to security.
When considering securing an IoT deployment, there are two separate conversations that need to be had. First, how do we secure the endpoint devices themselves, and second how do we secure the networks through which those devices communicate information back to a central source (or to each other).
The difficult part about this discussion, is that you can tackle it in many different ways. There are a few key architecture decisions that you’ll have to make to decide how both network security and endpoint security should be approached.
Dedicated Gateway Architecture
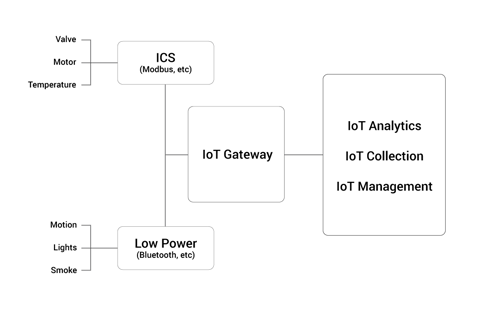
In this architecture, you’ll use a dedicated gateway as an aggregation point for all of the data coming from your endpoint devices. Each endpoint speaks to the gateway, the gateway aggregates and preprocesses all information, and then transmits it to a central source.
Technical details:
From endpoint device to edge gateway:
Typically, in this type of setup, you’d have all your devices connect over something like 802.1x, a wireless network authentication protocol.The identity of the device is confirmed based on a certificate provided by a RADIUS server.
This particular protocol offers encryption between the endpoint device and the edge gateway to ensure that communications between the two are secure should someone be eavesdropping.
Securing wireless communications at the physical layer is one of the primary benefits of 802.1x.
Using the Extensible Authentication Protocol (EAP), 802.1x provides a secure method for over-the-air network authentication. As such, it has become the standard for use on both wired and wireless LANs.
It can be configured for EAP-TTLS/PAP and PEAP-MSCHAPv2 credentials as well as digital certificate credentials through EAP-TLS.
From edge gateway to central or cloud data center:
When communicating between the edge gateway and wherever centralized storage or processing of data is happening, a VPN connection is a must.
In this case, you can choose to use either a software or hardware VPN to secure communications back to the central server. In many cases hardware-based VPNs have many benefits in this kind of architecture including:
- No specialized software is required on the gateway device itself.
- No software compatibility concerns: Because no software is required on the gateway device, there is no concern about which versions of applications or operating systems are running.
- In many cases, the gateway device itself can simply be a hardware VPN.
- Firewalling and isolation: A hardware VPN can act as a firewall between the gateway and the outside world. No other devices on the same network as gateway can even see that the endpoint devices communicating with it even exist.
- Greater control over where traffic is sent: A hardware-based VPN can be configured to only allow traffic to flow to a single endpoint. Meaning, when used as a gateway, it can ensure that any and all traffic can only go to the central network.
- Hardware VPNs offer a solution for securing wireless communications at the physical layer.
When to use it:
This architecture option is a good fit for IoT deployments in which devices are physically close to each other and operating with low power requirements. When devices are separated far enough physically that they can’t operate off the same wireless network connection, this type of architecture doesn’t work.
It is also harder to manage and monitor the behavior of each individual endpoint device in this type of architecture. Once information is sent to the centralized server, where anomaly detection security solutions are usually deployed, all of the data has already been aggregated and there is no granularity on what is happening at the individual device level.
It is, however, possible to implement some form of anomaly detection at the gateway itself if desired. Typically IoT devices are relatively simple in their function making it easy to build a behavior profile and execute simple, passive anomaly detection at the gateway entrypoint.
The bottom line: The centralized gateway architecture is a good fit (and typically lower cost option) if you have an IoT deployment with small physical footprint, and it isn’t imperative to know exactly what each individual endpoint is doing once the data reaches the central server.
Individual Device Communication Architecture

In this type of architecture, the endpoint IoT devices communicate directly with the centralized server or cloud data warehouse, rather than using a gateway to gather and aggregate communications.
Technical details:
In this setup, you’ll want to make sure you are encrypting all traffic from the endpoint device back to the centralized network.
Deployments like this often have to communicate across cellular networks or the open internet to communicate back to the centralized server (as they are often physically spread out across a large area).
Because of the networks in use, which are often untrusted, encryption of the data being sent from the endpoint device back to the primary network is very important. You’ll typically want to build it directly into the APIs you are using for the device itself, and often Transport Layer Security (TLS) protocol is used to achieve this.
You’ll also want to follow some best practices for traditional endpoint security including:
- Employing full disk encryption,
- Using a Trusted Platform Module (TPM) for storage
- Making the file-system read-only (to prevent bad actors from changing information on the device should they gain access), and
- Monitoring for file integrity.
When to use it:
This architecture is a fit for larger scale deployments but usually comes with larger costs than the centralized gateway architecture.
The type of backhaul you use will typically be the most expensive part of the equation. Typically these deployments are using Private LTE, 5G, or 4G networks to communicate.
You’ll also have to consider powering your devices, particularly if something like changing batteries is a prohibitive issue. Typically devices are set to send small amounts of data every so often so as not to overtax the available power source.
You do, however, get the benefits of being able to more centrally monitor, control and detect anomalies on each individual device at the central server.
In terms of security, there is a much larger attack surface in this model, as the endpoint devices themselves are more accessible to bad actors, and there are more connections from the point of data collection back to the centralized server to keep secure.
Combining VDI & VPN for Remote Work
If your organization is looking to implement a company-wide, secure solution for remote work that is not overly expensive, difficult to manage or maintain, and simple for end users, a combination of VDI and a hardware VPN may be the right fit.
Combining Virtual Desktop Infrastructure (VDI) with a secure hardware VPN would allow your employees to securely connect to your corporate network from their own devices.
A VDI allows end users to work remotely through a virtualized environment that lives on your central server. End user devices connect via the VDI to virtual machines that you have set up on your server, allowing users to execute work as if they are on your internal network.
With VDI, no data is stored on the end user device. Instead, the user can simply see what is on the screen of the virtual machine and interact with it, but not store data from it. VDI supports a range of end user devices, from laptops and desktops to tablets or mobile devices.
Combining this environment with a secure hardware VPN, like Archon's GoSilent Platform, protects all traffic and information flowing across the connection between the end user device and the central network.
Read the full article on combining VDI and a hardware-based VPN for more information on how it works.
Remote Access for Plant Operators
Using a similar architecture to the example above a VDI and VPN combination can be especially useful for allowing remote access to Human Machine Interfaces (HMIs) inside manufacturing plants.
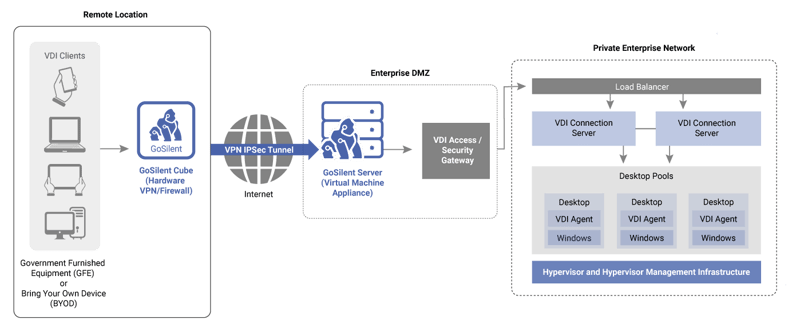
This allows a technician to remotely track the performance of plant equipment, and alert feet-on-the-ground maintenance staff if physical work is required to that equipment. The use of a VDI interface can allow that technician to remotely tune settings as needed to keep the equipment humming along effectively, without ever actually pulling sensitive data and storing it on a device outside of the plant.
This deployment option also nicely affords the ability to limit the traffic that can get through to the HMI. With the right hardware VPN, you can enforce a rule that only allows VDI traffic through.
All of this keeps the HMI from ever being exposed to the outside world.
Securing and Updating Unmanned Systems
IoT deployments that contain unmanned systems or endpoints are often the most difficult to secure, as denial of service attacks are prominent and very difficult to prevent in these scenarios.
Denial of service attacks are especially effective on IoT devices as they typically have limited computing power, making it easy to overwhelm them with traffic. This limited computing power also means that running tools on the endpoint to catch and stop denial of service attacks isn’t feasible.
For deployments like this, there are a number of options you have for tightly securing and protecting unmanned systems:
Cloud Delivery Networks
Using a good Cloud Delivery Network (CDN) is often the first step in helping to prevent denial of service attacks. Akamai, for instance, is best known for preventing one of the largest denial of service attack attempts in history.
Segregation of IT and OT networks
Another important option you can look into in this case is segregating your IT and OT networks. This means you essentially set up two separate networks, one for IoT devices to transmit data back to a central source for storage and analysis, and a second network specifically for managing and controlling the IoT devices.
Companies like Owl Cyber Defense build products called data diodes specifically for this purpose, that only allow IoT devices to communicate one-way, and prevent traffic from flowing in the wrong direction.
Once you’ve appropriately separated the network functions, you can focus all of your security efforts on the management network, as that is where the threat truly lies. Locking that network down and limiting access to it will prevent attacks that can render unmanned devices useless.
Using an edge gateway
Using a dedicated gateway architecture model (if possible with deployment size constraints) can also help here, by placing a more powerful security device between the outside world and the endpoint devices themselves.
IoT device security measures
There are a few things you can do on the device itself to improve individual IoT device security.
Reserve resources on the CPU or save disk space for your most critical services and functions. Make sure that the processes the device needs to function own a set partition of the CPU, for instance reserving 10% of the CPU for the remote management functionality. This helps make sure that if a denial of service attack is happening, you can still access and fix the device.
Make sure that you have a good mechanism in place to send and execute firmware updates for your device as well. Keeping devices in the field up-to-date goes a long way in keeping doors closed for unauthorized access.
Securing Legacy Industrial IoT Deployments
Another common problem that IoT deployments come up against is the use of outdated or legacy technology. Often the desire to connect equipment or endpoints that were never built to be connected comes up in the predictive maintenance and automation area of IoT.
Compatibility concerns
The biggest issue that tends to arise here is compatibility. Most modern cyber security technologies won’t work with the outdated or legacy technologies in place in most warehouses and factories.
In this case, your methods for securing these solutions become much simpler out of necessity. Purely because most of your options won’t work with the existing technology, you are usually left with using hardware-based VPNs to secure legacy IoT communications.
Often these particular deployments are a great fit for the dedicated gateway architecture as they are limited in geographical scope and need to protect legacy devices from outside networks.
Anomaly detection
It is ideal to use passive anomaly detection on the edge gateway in this example, as your device behavior will be very predictable. Because these devices were never envisioned to be connected and communicating, you can make sure their communications are very simple and repeatable, making it easy to catch anomalies in their activity.
Microsegmentation
You can also employ a strategy called microsegmentation to keep communication between devices limited to only those that need to speak to each other. Rather than allowing every device to talk to every device on the network, you can build and layer separate communication networks between groups of devices.
This can prevent devices from causing problems for each other on the network and reduce the available attack surface should someone gain unauthorized access to one of the smaller segmented networks.
Segregation of IT and OT networks
This is another case, similar to above, where segregation communications between IT and OT networks is also valuable.
Securing Connected Products in Regulated Industries
As a product provider who wants to have products “phone home” to alert for problems or maintenance issues, it is important to keep in mind the places your product will be used. If your product is deployed in highly regulated industries, like a machine that is used in factories to produce military aircraft for instance, the security of those “phone calls” home is very important.
In these instances you’ll most likely run into regulations that require something like a data historian. This is a program that records all production or process data as a time series, making it easy to look back over a timeline of records.
Segregation of IT and OT networks
This is another case, similar to above, where segregation communications between IT and OT networks is also valuable.
In this case you’d want to use something like a data diode to control communications between SCADA systems or industrial devices and end-users outside of the security perimeter of the plant.
Additionally, using tools specifically built to create a firewall between your IT and OT networks, like the Dragos Platform, helps to segregate and control any communications to and from your product in the field.
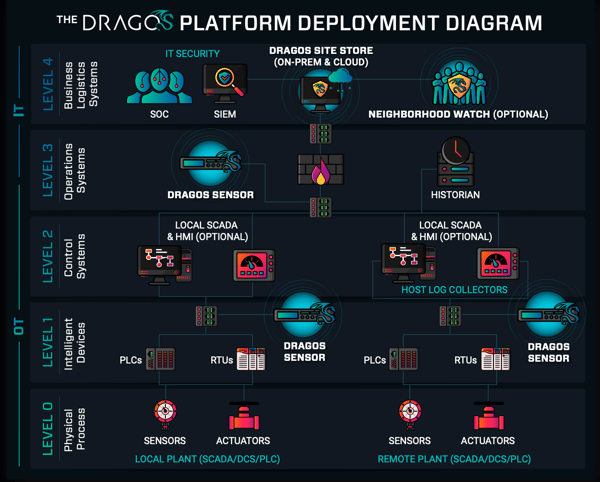
(source)
All of the complexity you’ve read about up until this point is exactly why a specific set of organizations have emerged: IoT Integrators.
What is an IoT Integrator?
An IoT integrator is a service provider that can help design, architect and build an end-to-end IoT solution.
IoT Integrators can be generally grouped into three major categories:
- Major & boutique consulting firms: This category is comprised primarily of consulting firms that focus on either enterprise system integration or specifically on industrial IoT. You’d find major consulting firms like Deloitte, KPMG and PwC in this category, as well as some smaller boutique firms like LNS Research and ARC Advisory Group.
- Technical organizations with consulting services: Many large technical organizations have consulting arms that help customers implement IoT solutions that include their products. Examples in this category include HPE, Dell, Honeywell and GE.
- Design & development organizations: Organizations in this category actually specialize in custom development of IoT solutions and may also help to integrate products to build full scale solutions. An example in this category is EPAM.
Using an IoT Integrator can significantly decrease your learning curve and help you implement a solution much more easily than trying to go it alone. Their expertise and experience is incredibly valuable in helping get large projects off the ground and completed successfully.
Clearly IoT security is of paramount importance as we continue to push the boundaries of what devices we can connect, and the data that we extract from those devices. The power of that data is alluring, and the ease with which we can extract and communicate it makes for an attractive proposition.
The trade-off we will always have to consider is how we can do all of these things securely, and avoid intrusion by those willing to do harm. While the debate between security and convenience will be waged until the end of time, there are plenty of secure solutions that are also beautiful in their simplicity.
And many of these solutions can help take your IoT deployment idea from dream to reality.
Contact Us
