National Information Assurance Partnership (NIAP)
NIAP Approved Solution for Remote Access
NIAP certification is a commercial cybersecurity product certification that is mandated by federal procurement requirements (CNSSP 11) for use in U.S. National Security Systems (NSS). Its primary purpose is to certify commercial technology or products which will be used to handle sensitive data.
Archon’s GoSilent is NIAP-approved for use under the VPN Gateway Protection Profile.
How it Works
The SilentEdge Enterprise Server is a dedicated server that acts as the centralized management and external access system for all GoSilent platforms integrated into one system.
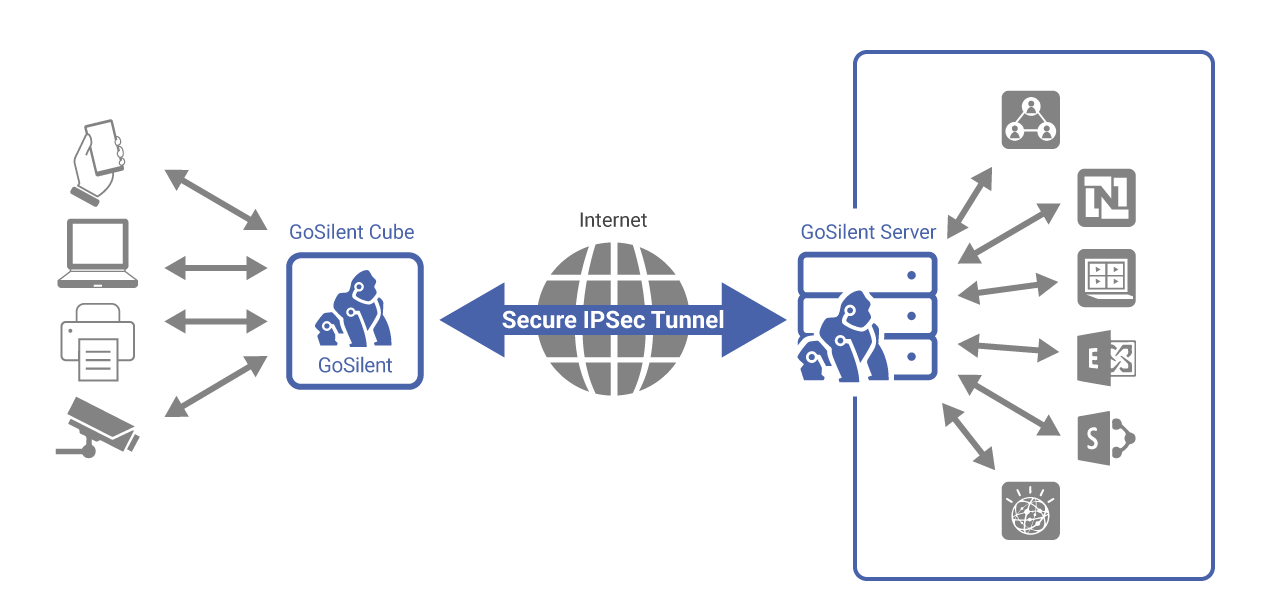
This platform allows for control over the configuration of SilentEdge as well as the GoSilent platforms. Operationally, it acts as the central peer for all IPsec connections from the GoSilent devices and provides gateway connectivity to external systems from the platforms located behind a GoSilent Client.
Together, GoSilent and SilentEdge provide a secure communications path to one or more systems located “behind” each GoSilent. These systems may connect to GoSilent via physical Ethernet. Each GoSilent establishes an IPsec VPN to the SilentEdge, and all traffic from the user systems is routed over that VPN. Physical Ethernet is supported on the VPN side of GoSilent.
NIAP Certification Information and Resources
Approved for use in National Security Systems
GoSilent is a commercial technology or product which can be used to handle classified data.
Less Expensive than Type 1
NIAP-certified commercially available products are generally less expensive than their COMSEC/Type 1 counterparts.
Easier to Use than Type 1
Typically more user-friendly than their COMSEC/Type 1 counterparts and have greater flexibility to integrate with various platforms and systems.
NIAP Reviewed & Approved
All claims for security features and capabilities have been evaluated and confirmed by a neutral third party.
Common Criteria for Stateful Firewall
Stateful layer 7 application firewall offers data packet filtering and is capable of tracking information flow states.
Common Criteria for VPN Gateway
IPSec IKEv1 & 1KEv2 with pre-shared keys and Top Secret (TS) level cryptography for the secure transmission of classified data
What is the process for NIAP certification?
In order to obtain NIAP Certification for a product, manufacturers must go through all of the following steps:
- Engage and establish a contract with an accredited national laboratory;
- Select Target of Evaluation (TOE), a product or system that will be the subject of evaluation;
- Choose the appropriate NIAP Protection Profile(s) they fit within;
- Establish a Security Target (ST), a set of security requirements and specifications to be used as the basis for evaluation (You can view Archon’s Security Target as an example);
- Submit a package with all of the above information to the NIAP office;
- Receive approval to start the evaluation process from NIAP office (at this point, the product will be placed on the NIAP in-evaluation list);
- Complete required documentation and testing with the previously-selected lab and submit all completed testing results to the NIAP office;
- Receive final certification from NIAP and CCEVS.
Once all of these steps are completed, the product will have a NIAP certification and will be placed on the NIAP Product Compliant List (PCL).
Learn More
What is the Common Criteria?
NIAP is responsible for U.S. implementation of the Common Criteria Evaluation and Validation Scheme (CCEVS). CCEVS is an internationally recognized set of guidelines (ISO 15408), which defines a common framework for evaluating security features and capabilities of Information Technology security products against functional and assurance requirements.
The CCEVS were developed collaboratively by the governments of Canada, France, Germany, the Netherlands, the UK, and the U.S. There is a mutual recognition agreement, called the Common Criteria Recognition Agreement (CCRA), whereby each country recognizes completed evaluations against the Common Criteria standard done by other parties.
NIAP is also responsible for running the validation body which certifies that products have effectively applied the CCEVS.
According to NIAP, “all products evaluated within the Scheme must demonstrate exact compliance with the applicable technology protection profile.”
As a neutral third party, NIAP assesses the results of the security evaluation, and if successful, issues a validation certificate to the product manufacturer. At that point, the product can be placed in the U.S. NIAP Product Compliant List and the international CCRA Certified Products List.
Learn More
Contact us.
